Current situation
With the rapid development of information technology in the country, universities, governments and enterprises have continuously increased Internet/Intranet-based business systems, such as various online filing systems, online approval systems, OA systems, and mail systems. The nature of the system's business generally requires the implementation of user management, identity authentication, authorization and other essential security measures; and the emergence of new systems, in the integration or integration with existing systems, especially for the same user group, There may be the following:
1. Repeated construction: Each application system has an independent user management system;
2. The user type is complicated: in addition to the teachers and students in the school, there are also off-campus users, external system development users, etc.;
3. Users need to memorize multiple accounts and passwords, which is extremely inconvenient to use and can easily cause multiple security risks.
4. Decentralized management mode, high cost and low efficiency; unified authentication and authorization cannot be realized. Multiple identity authentication systems must make security policies be set one by one in different systems, so the progress of modifying the policy may not keep up with the strategy. Change; it is also prone to management negligence and security breaches;
5. It is impossible to analyze the user's application behavior uniformly; therefore, for applications with multiple business systems, a unified identity authentication system needs to be configured to achieve centralized and unified identity authentication and reduce the cost of the entire system.
The purpose of the single sign-on system is to provide centralized and unified identity authentication for the application system, and achieve the goal of "one-point login, multi-point roaming, plug-and-play, application-independent", which is convenient for users.
Problem to be solved
Due to the urgent situation, it is urgent to fundamentally change this situation, and the following problems need to be met or solved:
1. Technology needs to comply more with the relevant requirements of laws and regulations, and consider further protection of personal privacy.
2. The perception of business is more agile, the access of teachers and students and partners is faster, the integration of B2B is higher and the response to change requirements is more agile.
3. The business needs to provide more secure protection, including the protection of identity privacy, the necessity of identity management, the urgency of access control and the necessity of auditing. Therefore, a complete and unified security solution is imperative.
In addition to the above mentioned aspects, there is a need to address: no need to integrate with any product, to solve common security issues across applications and data, but also to protect business processes and Web services (SOA). It also protects the data in transit and the data at rest, enhances the detection and prevention of internal and external threats, and is hot-swappable and based on industry or national standards across leading applications and with Loosely coupled coordination of web servers, application servers, portals, databases, and other IT systems.
Unified security platform features
The unified authentication platform must meet or at least provide four basic features of Authentication, Authorization, Audit, and Account Management. Single sign-on and logout and user and password should be secure and easy to use. Southwestern University of Finance and Economics used Oracle and open source software to build a campus security unified identity authentication platform.
Introduction to identity management platform
Introduction to identity management
Oracle Identity Management, according to its official description, is a complete and integrated next-generation identity management platform that delivers breakthrough scalability that enables organizations to quickly protect sensitive applications and data while complying with regulatory requirements. It enables organizations to effectively manage the identity of users across all enterprise resources and the end-to-end lifecycle of these users, both inside and outside the firewall and in the cloud.
The identity authentication service is the core part of the entire system, controlling all remote users' access to the network and application systems, providing comprehensive authentication, authorization and auditing services. When the user logs in to the system, the smart card is plugged in, and the remote authentication server is communicated through the secure encryption channel. The authentication server completes the authentication of the user identity, and obtains the identity of the current user and the authorization information of the system.
Oracle Identity Management Platform (IDM) includes identity management, role management, access control management, Weiservices management, directory service management, audit management and platform security. Its logical architecture is shown in Figure 1.
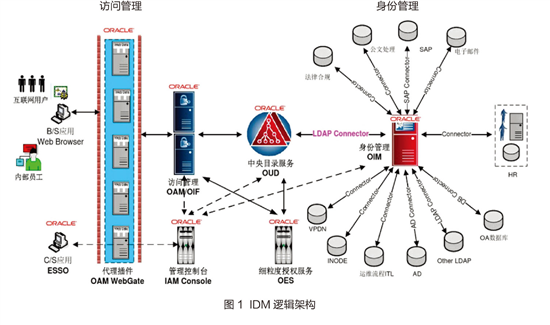
Oracle Identity Management 11gR2 consists of three components: Identity Governance, Access Management, and Directory Serclevices: Identity Management includes providing user registration, access requests, role lifecycle management, and user configuration. , access authentication, closed loop control and privileged account management. Access Management provides features such as authentication, single sign-on, identity authorization, federation, fraud detection, and mobile and social login. Directory services provide features such as virtual directories, LDAP storage, metadirectories, and synchronization services. The characteristics are as follows: 1. centralized account management; 2. centralized identity authentication management; 3. centralized authorization management; 4. centralized log audit management; 5. centralized log audit management.
Because the entire Oracle identity management involves a lot of content, here, only the unified identity authentication and authorization, that is, single sign-on, is introduced.
OAM introduction
Oracle Access Management is a Java Enterprise Edition (Java EE)-based enterprise security application that provides comprehensive Web perimeter security and Web single sign-on services, including identity context, authentication and authorization, policy management, testing, Risk analysis and auditing, and limited access to confidential information.
Single Sign-On (SSO) is a single sign-on. In multiple applications, users only need to log in once to access all trusted applications. Under this condition, the administrator can easily implement the desired security control without modifying or interfering with the user login.
Oracle has two sets of single sign-on solutions: Oracle Access Manager, Oracle Single Sign-On Server (OSSO). Oracle officially recommends Access Manager as a solution for SSO. Advanced users of Oracle Single Sign-On Server will eventually recommend migration to the Oracle Access Manager solution. This article only describes the way through the OAM Agent (WebGate). For other ways, please refer to the Oracle related documentation.
1.OAM component
OAM consists of the following three components:
Access Server: A stand-alone server that provides authorization, authentication, and auditing services for Accesgates. It comes with OAM.
WebGate: Intercept HTTP requests and redirect them to AccesServer for authentication and authorization.
Identity Assertion Provider (IAP): A type of security provider that asserts a user's identity by verifying the information in the generated cookie.
2.OAM function
OAM provides the following features for enterprise applications: authentication, identity management (through integration with OID), access control and authorization, access auditing, single sign-on.
3.OAM single point
Login Process In general, the user will access the program running in Weblogic through the browser. Oracle HTTP Server (OHS) will use OAM Webagte to intercept the request sent by the user, check whether the resource is a protected resource, and Go to OAM's Policy server for authentication. After OAM successfully authenticates the user, OAM will generate a session credential, a cookie, which can be compared to a single sign-on token. After obtaining the token, OAM will use the IAP to assert and authorize according to its identity information, and return the corresponding request resource according to the authorization level and the authorization result.
From its principle, we know:
1. OAM mainly does two things: (a) verifying the existence of a single sign-on cookie; (b) checking if the requested resource is protected.
2. WebGate is a plugin for the web server that intercepts HTTP requests and directs the request to Oracle Access Manager (OAM) for user authentication.
3. Oracle OAM stores the user's information through cookies, and then implements a single point access to the credit station through cookies.
Concrete practice of building enterprise-level unified identity authentication and integrated access control
In the information construction of colleges and universities, from the digital campus to the development of smart campus, it is necessary to establish a unified, secure and controllable identity authentication and management centralization, identity management virtualization, and protection of application system security for unified identity authentication and management. platform. Southwestern University of Finance and Economics unified identity authentication authorization management strategy authorization logic architecture diagram shown in Figure 2.
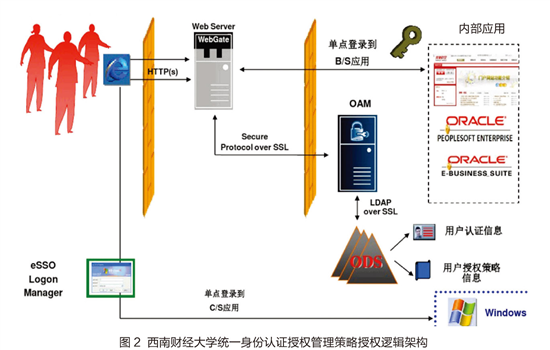
Architecture and deployment of integrated security access control
As shown in Figure 2, in the user access layer, Nginx is used as a proxy acceleration service, combined with NGINX, OWASP-MODSECURITY-CRS. OWASP-MODSECURITY-CRS is an open source, efficient, low maintenance rule Nginx Web Application Firewall module. Its main goal is to harden web applications against SQL injection, cross-site scripting, cross-domain forgery requests, local and remote file inclusion vulnerabilities, and SSL certificates. All access forces SSL to be enabled and completed at this level. Therefore, this layer can be architected on the boundary of the IDC.
Management of user account resources through CRM
CRM is both a management philosophy, software and technology, and an application system. The technologies used in CRM include Web, database, data warehouse, data mining, and so on. A complete and effective CRM application system consists of four subsystems: business operation management subsystem, customer cooperation management subsystem, data analysis management subsystem and information technology management subsystem. Southwestern University of Finance and Economics adopts the open source software SuagrRM as the basic platform to carry out in-depth secondary development to meet the needs of the school's two campus information construction, and to provide more comprehensive and convenient information services for the teaching, management and life of the school teachers and students.
The school provides a unified identity for each registered faculty, general students (including undergraduate and graduate students, international students, exchange students) and alumni, and provides users with appropriate networks based on the unified identity authentication account and its corresponding authority. Information service.
OUD deployment
OUD is an all-in-one directory solution for Oracle's unified directory and storage, agent synchronization and virtualization capabilities. It provides the services needed for all high-performance enterprise and carrier-grade environments. A unified catalog, ensuring scalability, with billions of entries, easy installation, flexible deployment of enterprise management and effective monitoring. The OUD server works according to a separate LDAP directory service daemon (slapd). The copy (import) service is also done with the support of the Unix daemon.
New features in OUD 11gR2: 1. Location-based search for social networking applications; 2. Oracle database enterprise user security support (EUS); 3. Out-of-the-box JVM; 4. Compatible with Oracle Directory Server Enterprise Edition and coexistence or Transition to replication between OUDODSEE and OUD; 5. Ability to move systems between test and production environments; 6. Identity store Oracle's IDM products.
OAM deployment
OAM provides Oracle Access Management with an innovative service that complements traditional access management capabilities. For example, Adaptive Authentication (SSO) federated single sign-on, risk analysis and fine-grained authorization extend to mobile clients and mobile applications and access portals, allowing customers to build their own private cloud SSO services. Services can be licensed and enabled as needed to meet the specific needs of the organization. The services provided by the server on the access management are hosted on the Oracle WebLogic server, the defense access management interceptor and filters (access management WebGate, Web services and API gateway), and the mobile and social service client SDK, which can be installed as needed. On mobile devices and on PCs (desktops and laptops).
Database layer introduction
In order to ensure the efficient, safe, stable and friendly service of the whole system, considering the difficulty of maintenance in the later stage, we use the dual-master master-slave hot standby architecture for the database Oracle and OUD. And use OracleEM (Enterprise Manager) for operational monitoring and health check of the entire system.
Modification of the application system
Based on the principle of minimum impact on the transformation of existing application systems and the principle of security and stability, we adopted the management and control of most application system domain names such as OA system, mail system, personnel, student-related affairs, and educational affairs, and directed all of them to The user accesses the access layer. The application system only needs to obtain the special identifier contained in the HTTP header sent from the authentication system (OAM), and almost no other code is changed. At the access layer, log auditing and security detection filtering are enabled.
Through practical application testing, it is found that:
1. Its architecture's good scalability and concurrent processing capabilities can be well placed to cope with the load such as the peak of the course selection.
We used 4 OAMs for load balancing, and the back end uses Oracle RAC. All applications currently have more than 20 integrations. RedHatAS6 and OAM+OUD are deployed in VMWare environment with 32GB of single memory. After stress testing, you can get 4000 times / sec, fully meet the application on campus.
2. The application system is small. Because only the code of the certification department is needed, the characteristic value of OAM is included in the HTTP header. Therefore, it is only necessary to modify a small number of authentication codes to quickly and efficiently integrate seamlessly to achieve single-point authentication.
3. Security is good, hiding the application system behind the WebGate cluster, effectively reducing security risks.
In summary, after the system architecture is completed, users accessing any application system in the campus will be forced and loaded with the SSL certificate to the authentication login page. Thereby, centralized authorization and control are better realized, the maintenance in the later stage is reduced, and the user experience is also good.
Through the construction of the campus unified identity authentication and management platform, unified authentication management, unified authorization management, unified audit management and unified account management are realized, user-centric account lifecycle management is realized, and the unification of technical specifications is gradually solved. The management realizes the process and standardization, reorganizes the data in the information system, simplifies the account management work, saves the management cost, and promotes the improvement of the source system data quality. In addition, due to the boundary of the IDC, it is beneficial to protect the internal service security of the IDC.
(The author is the Information and Education Technology Center of Southwestern University of Finance and Economics)
Ergonomics has an important impact on product design, which directly affects the experience of product use; therefore, in product design, designers try to adhere to the principle of "humanization", so as to conform to the theory of ergonomics, so as to improve the comfort and experience of product use.
This ergonomic desk is designed with automatic lifting function and ergonomic design. At the same time, the hand controller also has multiple memory keys storage function, which can reach the height you want with one key.

Ergonomic Desk,Adjustable Ergonomic Desk,Ergonomic Standing Desk,Ergonomic Height Adjustable Desk,Adjustable Desk Standing
Suzhou Uplift Intelligent Technology Co., Ltd , https://www.officeliftdesk.com